WannaCry. Reveton. CryptoLocker. Fusob. CryptoWall. And more: BadRabbit, DarkSide, SamSam, etc.
We are talking about ransomware, computer viruses that take your data hostage. The hacker, the proponent of the attack, demands a cash ransom to give you back your data.
But what is ransomware? How does a cybercriminal hack your system? What are the most common types of ransomware attacks? And how can you prevent a ransomware attack?
If you are the CEO, CIO or IT manager of a company you are surely aware of the seriousness of the ransomware threat — a global threat that, according to the U.S. cybersecurity agency CISA, knows no crisis.
To help those like you who are looking for actionable advice on how to face this issue, we've written this practical guide to ransomware from A to Z. Inside, you'll discover:
- What ransomware is
- How ransomware gets into your system
- How to prevent a ransomware attack: 5 strategies for 2025
- Ransomware: most common types
- How to ensure ransomware recovery, or in other words: how to restore files encrypted by ransomware.
Let's get started.
#1 What is ransomware?
Ransomware is a type of malware that takes a victim's data and/or devices hostage and releases them upon payment of a ransom, usually in bitcoin. To date, ransomware represents one of the most insidious threats to a business.
Related reading: How does ransomware get in? 7 attack vectors companies should know
The growth of ransomware attacks is exponential. In 2019, a company fell victim to ransomware files once every 14 seconds; in 2021, every 11. By 2031, Cybersecurity Ventures forecasts one company every second.
Economic loss due to ransomware is steadily increasing. In the most extreme cases, companies can pay as much as $40 million to get their data back. According to cybersecurity agency Panda Security, the average ransom paid by ransomware victims has increased by 82 percent since 2020 to $570,000. Also, as per Coveware's report, the average downtime is 12 days.
Now that you understand what ransomware is and the damage it can cause, let's take a detailed look at the types of ransomware attacks that exist today.
#2 Ransomware: types
Behind every ransomware attack there is almost always human error. Just like any other hacker attack, a ransomware attack relies on social engineering before actual hacking. The attack is done by leading the victim into a trap or, more rarely, by exploiting security holes in one of the access points to the system itself.
Related reading: 7 different types of ransomware (& 23 examples of attack damage)
#2.1 Phishing
Phishing is not precisely a type of ransomware, but given that, according to IBM, 41 percent of ransomware attacks are based on phishing, addressing the topic in a practical guide to ransomware is a must. Today, cybercriminals conduct thorough investigations of a company's personnel before taking action. To identify potential targets, cybercriminals may monitor the company's website and then cross-reference the collected data with public social media profiles.

The purpose of this practice is to accumulate information in order to reproduce a login page to a site used by the victim that is identical to a page the victim frequently visits and trusts. To gain access, the victim will give their credentials without realizing that they are providing them not to the site but to the hacker.
Once in possession of these data, the hacker has access to the victim's device and, consequently, to any computer system within which the victim is logged in by default with root privileges. Even if the victim is not logged in by default, the cybercriminal can still exploit the data on the victim's device to do a dictionary attack or the like and extract unsafe usernames and passwords. At this point, the hacker has complete access to the system and can encrypt any files on it.
#2.2 Scareware
Scareware is a type of ransomware that uses social engineering to scare a target into purchasing software they do not need. Often the scareware claims to have exposed the user to another form of malware. The easiest way to avoid scareware is to question any claim that the computer has been infected unless it comes from a reputable antivirus provider and is actually in use by the user.
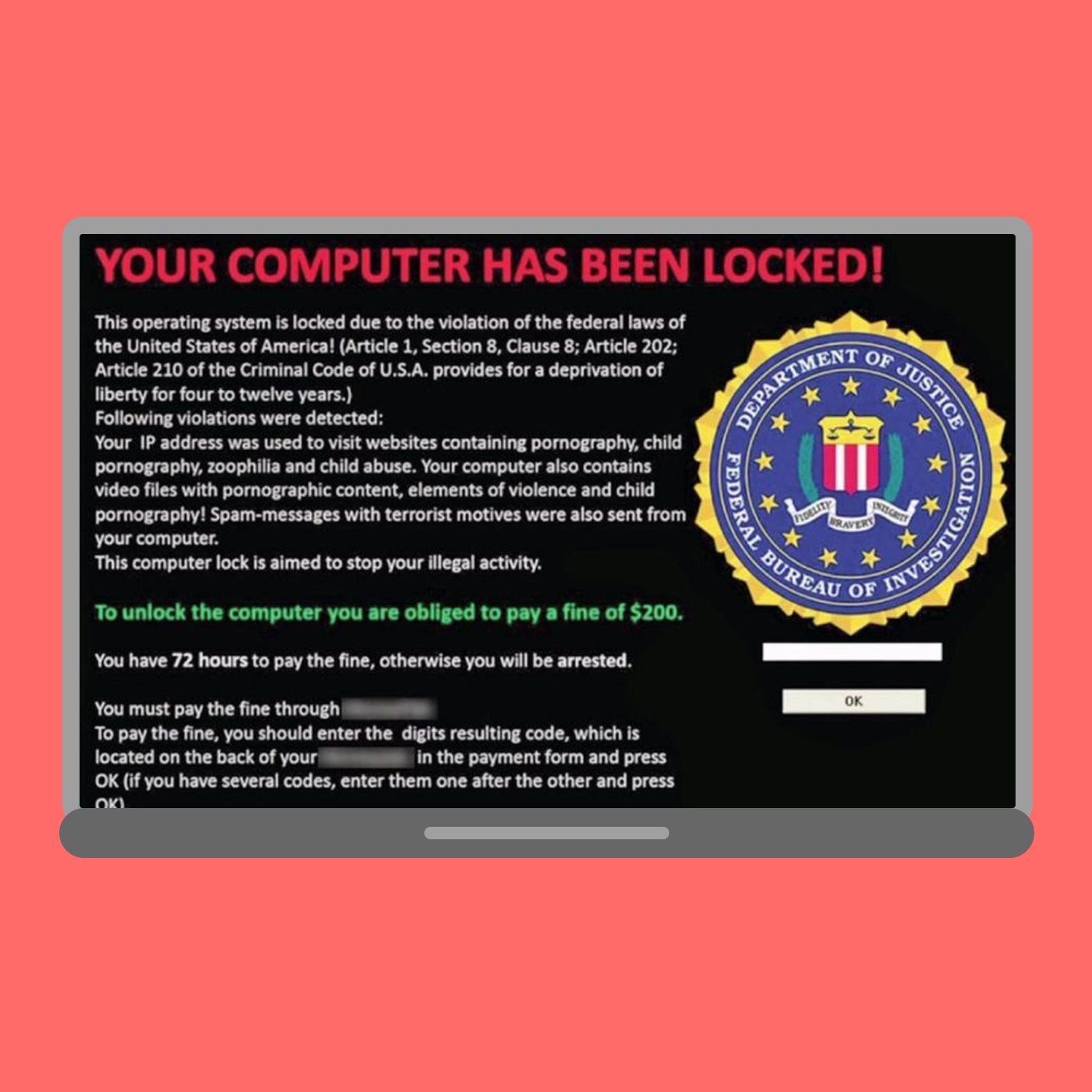
#2.3 Screen locking
Screen lockers lock your computer screen, making it impossible to access it. If you have been infected by a screen locker you will see a message on your screen demanding payment to provide you with access again. Usually, the message pretends to come from a trusted source, such as the police, a government agency, an Internet company known to you, or the postal service.
2.4 Cryptographic ransomware
Cryptographic ransomware is what we normally refer to when we talk about ransomware. Cryptographic ransomware uses advanced encryption algorithms to encrypt the data on the device. The victim receives an alert showing the ransom to be paid and the procedures to be followed to recover access to the data; this is usually a cryptocurrency payment. As with screen lockers and scareware, it is necessary to use a ransomware-proof backup strategy to restore files encrypted by ransomware.

#3 How to prevent a ransomware attack: 5 strategies for 2025
There are many security measures a company can take to prevent a ransomware attack. Among them, the 5 best practices to follow are:
#3.1 Disaster recovery plan testing
Nothing can ensure business continuity and disaster recovery like a proper ransomware-proof backup strategy. A ransomware recovery plan that allows you to restore encrypted files often makes the difference between losing all your data and recovering it in a very short time.
A sound disaster recovery strategy involves backing up data in a timely manner to one or, better yet, multiple locations. In addition, it must be easy to test since testing is the only method of confirming that the recovery time meets your business objectives. Last but not least, the disaster recovery plan must be able to recover data quickly and regularly, without surprises. When the ransomware file hits, you must make sure you can recover your data and continue working as soon as possible.
Want to learn more? [Article] Disaster recovery plan: 3 best practices for 2023
#3.2 Minimize attack surface through the principle of least privilege
The principle of least privilege preaches that each process, program, and/or user within the organization has visibility of only those resources immediately necessary for its operation. Applying this principle ensures that if an employee has been affected by ransomware, it will not automatically spread to the rest of the system.
A very common additional precautionary measure is to test unknown files or programs within a sandbox — an isolated testing environment that, in the event of an attack, limits the damage to the environment itself, reducing the risks of infecting the rest of the system.
#3.3 Prepare staff with proper security training
Training staff is a sine qua non for minimizing the risk of ransomware attacks. All it takes for an organization to be compromised is for one employee to let their guard down. That's why employees must be trained regularly on the possible dangers and precautions to take to protect their devices and their company (adopt a password manager, use a spam filter, don't open suspicious emails, configure desktop extensions, block malicious executables and Javascript files, etc.). In fact, to penetrate the company's computer system, it is often enough to penetrate an employee's computer.

Finally, it is essential to prepare and test a crisis management strategy, pre-assigning roles within the company and making sure that, in the event of an attack, every employee knows what to do so that he or she can act promptly.
#3.4 Implement the 321 backup rule
If you are unfamiliar with it, the 321 backup rule is the foundation of efficient data management. According to U.S. cyber security intelligence CISA, "all companies should use the 321 backup rule."
The 321 backup rule is a cross-media backup strategy to minimize the risk of loss and maintain access to critical backups while avoiding problems such as ransomware and natural disasters.
Why such a rule? Simple: With this simple stratagem, you can substantially reduce the risk of data loss by minimizing the chance that the failure of a backup copy will turn into catastrophic damage. To follow the 321 backup rule, it is necessary to keep:
- Three or more backup copies
- On at least two different media
- With at least one off-site copy
Want to learn more? [Article] 321 backup rule & hybrid cloud: diversify your disaster recovery plan for 2023

#3.5 Use a decoy
An unusual but extremely effective precautionary measure is to use "canary files." From the popular expression "canary in the coalmine," (which used to be used to identify tunnels without oxygen), canary files are files left exposed to an external attack and, therefore, intentionally more vulnerable than the rest of the system-on which monitoring software runs that constantly checks whether the files have been encrypted by ransomware.
The purpose of such a practice is to prompt the cybercriminal to reveal himself in a position of disadvantage so that he can nimbly neutralize the threat. Other devices, hard drives or assets can also be used as an alternative to a file.
#4 Ransomware recovery: strategies to restore encrypted files without paying the ransom
If you have fallen victim to ransomware you have two options:
- Pay the ransom
The goal of any ransomware is to put victims in a situation where paying the ransom seems the only solution. Whether or not to pay depends on each company's particular circumstances and carries considerable risk. In general, it is not advisable to give in to the cybercriminal's demands: according to Kaspersky, more than half of victims pay the ransom but only a quarter of them succeed in restoring ransomware-encrypted files.

- Restore files encrypted by ransomware with an off-site ransomware proof backup
A ransomware-proof backup makes it possible to restore files encrypted by ransomware quickly and surely. Nevertheless, ransomware always tries to encrypt not only files but also backups. Therefore, it is necessary to follow the 321 backup rule and rely on multiple off-site backups-which is why many rely on hybrid cloud and multicloud.
Related reading: What is multicloud? Examples and benefits in 2025
Another security measure in this direction is object storage.
This is because with object-based storage, object storage enables granular flexibility in terms of efficiency and cost while providing a higher level of disaster recovery and business continuity than file storage solutions. In addition, object storage fortifies enterprise cybersecurity through two innovative technologies:
- S3 Object Locking, a feature that prevents files from being modified prior to a set date, thus making it impossible for both the cybercriminal and the service provider itself to modify (and thus encrypt) the victim's files.
- S3 Object Versioning, which provides the user with a history of file changes, thus allowing the user to revert to any previous configuration at any time.
Related reading: How to get rid of ransomware (Instead of paying for it)
#5 Want to learn more?
With this article, you have discovered what ransomware is, the types, how to prevent it, and the basics of putting a ransomware recovery strategy in place.
Want to learn more? If you speak Italian, download the free practical guide to guaranteed ransomware recovery.
Don’t speak Italian? Contact us here >