Ransomware is malware that encrypts all the victim's data or systems and makes them inaccessible. Then, it asks for a ransom payment to unlock the hostage.
Therefore, IT leaders must follow the best practices of defenses (e.g., using versioned, immutable storage and backup data regularly).
However, sometimes, ransomware strikes, and we only occasionally have a fully updated data backup. At that moment, it's crucial to know how to decrypt files encrypted by ransomware.
After reading this article, you’ll learn the following:
- How ransomware encryption works
- The key insights to identify a ransomware strain (and its symptoms)
- Step-by-step process to recover from a ransomware attack
- How to decrypt files encrypted by ransomware (and recover your data even without a previous backup)
- 15 best ransomware decryption & removal tools of 2023
How ransomware encryption works
In a nutshell, ransomware encrypts the victim's files using symmetric and asymmetric encryption methods. The process is done correctly when the attacker generates a public key locally which is then encrypted using asymmetric encryption. Keys can be either single or multiple, relying on complex encryption methods like RSA. Finally, the ransomware encrypts data and makes it inaccessible.
The attacker demands a ransom fee to decrypt the files in exchange for the key. Payment is often required in cryptocurrencies like Bitcoin, which is difficult to trace.
Related reading: How does ransomware get in? 7 attack vectors companies should know
Sometimes, when the encryption is not done correctly, it can be broken through trial and error or by exploiting vulnerabilities in the algorithm. However, this can be time-consuming and difficult, and there is no guarantee that it will work.
That’s why, in 2023, it’s crucial to know how to decrypt files encrypted by ransomware properly and efficiently. Especially if you don’t have an updated backup at hand.
How to identify ransomware strain (and its symptoms)

Identifying the specific strain of ransomware (e.g., CryptoLocker) that has infected a system is crucial in determining how to decrypt files encrypted by ransomware. In particular, recognizing the strain can help IT managers, CTOs, and developers determine whether a known ransomware decryption tool is available for that specific case.
The first step to identifying it is to look for ransomware symptoms, such as files that are suddenly inaccessible, slow/unresponsive computers, strange pop-ups/alerts, and the appearance of ransom demand messages. Once we're sure that our computer is infected by ransomware, we must identify the specific malware strain.
One way to check the ransomware family is to use an identifier tool (e.g., ID Ransomware) that matches the file extension of the encrypted files or the ransom note message.
Another way to identify the ransomware strain is to use automated tools to analyze the malware's interactions with users and applications. For example, behavior-based techniques can help identify ransomware symptoms like API calls and unusual traffic.
Once the ransomware strain has been identified, it is essential to determine whether there is a known decryption tool available for that particular strain. The following sections will show some of the best ransomware removal tools.
It is also important to note that some ransomware strains are designed to be undetectable and may not have any known decryption tools available. In such cases, the only viable option is to follow a proven, step-by-step security procedure.
How to recover from a ransomware attack in 6 simple steps

[Don't have an updated data backup available? In the next section, you’ll learn how to decrypt files encrypted by ransomware.]
Recovering data from a ransomware attack can be a complex process. The following steps are recommended to help IT managers, CTOs, and developers recover from a ransomware attack:
1. Don't restore your backup immediately: Ransomware perpetrators know this and will also encrypt your newly restored data. Instead, get rid of the virus first.
2. Isolate and contain the infected systems: As soon as you become aware of a ransomware attack, it's critical to isolate the infected systems to prevent the malware from spreading further. Disconnect the affected computer from the internet and any external storage devices immediately, and check other computers and servers on your network for signs of encryption. Once you've confirmed which systems are affected, you can move on to the next steps.
3. Identify the ransomware and remove it: IT managers and CTOs should identify the type of ransomware that has infected their systems to take the most appropriate restorative actions. Look at the note left by the hacker or find help with an identification tool like ID Ransomware. Then, find a ransomware removal tool (we’ll see the best ones in the next sections) or seek professional help to remove it manually.
Related reading: How to get rid of ransomware (Instead of paying for it)
4. Determine if the attacker exfiltrated data: Some ransomware attacks involve theft. The attacker copies sensitive data before encrypting it and threatens to leak your confidential information unless a ransom is paid. For GDPR purposes, it's essential to determine if data was exfiltrated and, if so, what data was taken and to who it was sent. Especially if you were managing your customers' data.
5. Incident response report to law: Take a photo of the ransomware demand message and report the attack to the law — this will help identify the perpetrators of the ransomware attack and develop different prevention methods.
6. Rebuild and restore systems: If you have an external backup, wipe your systems completely to restore the original files. The backup should be from a date before the ransomware attack to prevent re-infection. It is important to note that removing the ransomware doesn't necessarily decrypt files or restore the original files. This can only be done using a ransomware decryptor if available for the infection variant. Also, remember to change all your passwords.
Related reading: 6 backup strategy solutions for ransomware data recovery in 2023
In addition to these steps, IT managers and developers should conduct a post-mortem analysis to determine how the ransomware attack happened. The goal is to minimize the impact of future episodes and ensure their systems and data are adequately protected.
Please note: the 6 steps listed above are crucial for a proper ransomware incident response. Yet, sometimes, even IT leaders don’t have an updated backup (or it was encrypted by ransomware, too). The following section will provide a simple, step-by-step process to decrypt files encrypted by ransomware.
How to decrypt ransomware encrypted files (and recover your data without a previous backup)
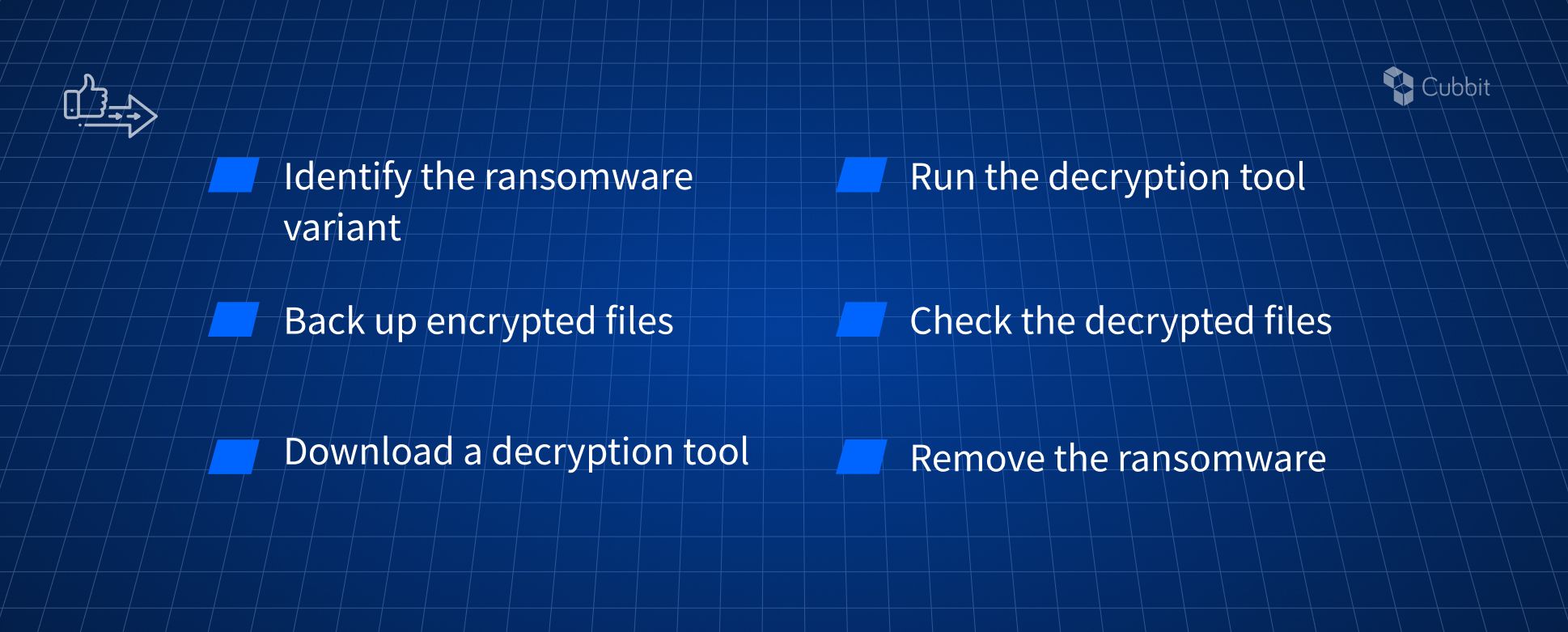
If you don't have an updated backup, you must face the ransomware and decrypt your files. Here's a 6-step framework:
Step 1: Identify the ransomware variant
The first step in recovering ransomware encrypted files is identifying the type of ransomware that has infected the system. This can be done by examining the malware's ransom note and file extensions. A website such as ID Ransomware can help identify the type of ransomware. Sometimes, there may be publicly available decryption tools for specific ransomware strains.
Related reading: 7 different types of ransomware (& 23 examples of attack damage)
Step 2: Back up encrypted files
Before attempting to decrypt files, it is essential to back them up if something goes wrong during the decryption process. It is recommended to make a copy of the encrypted files and store them on an external device or in the cloud.
Step 3: Download a decryption tool
If a decryption tool is available for the specific ransomware strain, download it from a reputable source like the website of the antivirus software provider or the No More Ransom Project. It is vital to ensure that the tool is compatible with the specific ransomware variant.
Step 4: Run the decryption tool
After downloading the decryption tool, follow the instructions provided by the device to decrypt the files. This may involve selecting the encrypted files, entering a decryption key if one is provided, or selecting a folder to save the decrypted files. It is essential to follow the instructions carefully, as the wrong settings or options may result in the decryption process failing (hence the importance of making a backup of encrypted data before starting this process).
Step 5: Check the decrypted files
Once the decryption process is complete, check the decrypted files to ensure they work correctly. Inspect the files with an antivirus program to ensure they are not infected with any remaining malware. Also, save the decrypted files to a secure location.
If the files are still not functioning correctly, try a different decryption tool or seek the help of a professional data recovery service.
Step 6: Remove the ransomware
After successfully decrypting the files, removing the ransomware from the infected system is crucial to prevent further damage. This can be done using antivirus software or following the instructions provided by other tools like the No More Ransom Project.
In conclusion, decrypting and recovering files encrypted by ransomware can be very technical, and there is no guarantee of success. It is essential to back up encrypted data, identify the type of ransomware, download a reputable decryption tool, follow the instructions carefully, and remove the ransomware from the infected system.
15 best ransomware decryption & removal tools of 2023

Before going further in this section is vital to specify the difference between a ransomware decryption tool and a removal one.
1. Ransomware decryption tool: it allows decrypt files encrypted by ransomware.
2. Ransomware removal tool: it removes the ransomware virus.
So, if you use the 'ransomware decryption tool,' the virus will still re-encrypt your files. On the other hand, if you remove the ransomware and don't have an updated backup, you will never reaccess your data.
10 best (and free!) ransomware decryption tools
Victims of ransomware attacks can use decryption tools to recover their files without paying the ransom or restoring the backup. Here are some of the best ransomware decryption tools available.
1. Bitdefender decryption tools: Bitdefender offers a ransomware recognition tool, plus a decryptor for ransomware like GandCrab, REvil, and Darkside.
2. Trend Micro ransomware file decryptor tool: If you need to decrypt files, a victim of Petya, Jigsaw, CrySiS, Teslacrypt, and other tricky ransomware. Go for this.
3. Emsisoft ransomware decryption tools: From Jigsaw to Wannacry, Emsisoft offers decryption tools for different types of ransomware.
4. The No More Ransom Project: Another flexible tool for decrypting files victims of Maze, Teslacrypt, REvil, GandCrab, and more.
5. Avast Ransomware Decryption Tools: Avast tool can decrypt data victims of different strains, such as Babuk, CrySiS, GandCrab, TeslaCrypt, and many others ransomware.
6. No ransom by Kaspersky: Kaspersky offers 7 free ransomware decryption tools for recovering data against Coinvault, Shade, and more.
7. AVG Ransomware Decryption Tools: AVG offers 7 free ransomware decryption tools for Apocalypse, BadBlock, Bart, Crypt888, Legion, SZFLocker, and TeslaCrypt.
8. Netwrkspider/WannaDecrypt: A free GitHub tool for decrypting 5 ransomware of the WannaCry family (WannaCry ransomware included).
9. Maureen Data Systems decryption tools: They provide decryption tools for numerous ransomware like TeslaCrypt and Dharma.
10. Quick Heal ransomware decryption tools: CrySiS, Troldesh, DeriaLock, GandCrab, and more: Quick Heal offers 20 free decryption tools.
Not finding what you were looking for? In this article, Heimdal Security provides the most thorough list I've ever seen on the internet.
5 best ransomware removal tools
Let's now consider the 5 best ransomware removal tools of 2023:
1. Avast Ransomware removal tool (100% free): It scans and remove ransomware on Windows, Android, Mac, or iOS device.
2. Bitdefender Antivirus Plus (30-day free trial | from $23.99/year): This behavior-based detection system wipes out all ransomware samples, according to PCMag.
3. MalwareBuster (Free trial | $35.99/year): A software that scans all your pc and removes every ransomware it finds.
4. Webroot SecureAnywhere AntiVirus (14-day free trial | from $23.99/year): Webroot is an antivirus that occupies tiny disk space and scans very quickly. In the test run by PCMag, it wiped out every ransomware and restored encrypted files.
5. Zscaler (30-day free trial | from $28.80/year): A cloud-based platform that features malware removal tools.
Conclusion

Ransomware attacks are on the rise, and they can be devastating to businesses and individuals.
This article has provided a comprehensive overview of how ransomware works, the key insights to identify the different malware families, and the necessary steps on how to decrypt files encrypted by ransomware.
Dealing with a ransomware attack can be a nightmare, but paying the ransom only funds criminal activity, and there's no guarantee you'll get your data back. Instead, acting quickly and following the steps outlined in this article is crucial to minimizing the damage.
Remember, prevention is always the best cure.
Cubbit offers a backup solution for ransomware data recovery with its geo-distributed, secure, S3 compatible, and immutable object storage — at 80% less than AWS.
Each stored data is encrypted, micro-fragmented, and geo-distributed in multiple copies in a peer-to-peer network under user control. Cubbit provides a simple and S3 compatible UX, making it easy to switch from AWS to Cubbit by changing one configuration parameter in the CLI.
You can activate a cardless, free trial of Cubbit object storage here.
P.S. For a more customized solution or to get advice on storage and cybersecurity, get in touch with our team.