In a world where we got used to entering the same password for every service we sign up to, and where we allow systems to memorize our keys, two-factor authentication becomes a vital tool to protect access to our data.
On this page, you’ll find:
- What two-factor authentication is and how it works.
- 3(+3!) interesting cases of two-factor authentication applications.
- How to set it up on the Cubbit cloud.
What is two-factor authentication? A definition
Nice introduction, but… what is two-factor authentication?
In a nutshell, two-factor authentication (2FA) is a method that adds an extra layer of security to verifying your identity when you log-in: by asking you to use two different authentication methods successively, it protects from strangers who know your password and from brute force attacks.
We’re generally used to log-in by entering our usernames and a password, this process is called single-factor authentication. When we talk about 2FA two types of credentials are required in order to access our account. These are the different types of verification used as 2nd step:
- biometric (something you are - e.g. fingerprint, facial recognition).
- An additional password (something you have or know - e.g. credit card security code, a visual pattern).
- An identification method sent through another previously validated channel (e.g. mobile-phone, email).
- Location-based (somewhere you are - e.g. if you log-in from an unusual location you’ll be asked to verify yourself in an alternative way).

Why two-factor authentication is important
We have defined what two-factor authentication is, but why is it so important?
We surf on the internet every day and are progressively more and more dependent on it. We become so immersed in the flow of things that we act automatically. This means becoming impatient at the drop of a hat, and it also amounts to using the same password for every service we sign up to with the aim of emptying our minds while we pursue mental-recharging between repetitive clicks on our social media channels.
But when we use the very same password for our Snapchat and cloud account the chasm is crossed. It’s time to come back down to earth: the exact key, used to access a service that can be easily spoiled, is a very weak point that can lead to our data being stolen by strangers (or even an entire company if just one employee is a victim).
Then, two distinct scenarios can occur:
- a direct data-breach to the not-very-secure service (e.g. Snapchat) leading to the password discovery by strangers. The result? All private data stored in your cloud becomes publicly accessible and most likely sold on the dark-web. Have I Been Pwned is a popular website to check if some of your account passwords have been stolen and are now being sold on “the other side of the internet”.
- You use the very same (or even similar) key in a service (e.g. Hotmail) that allows you to recover the password by answering a question easily knowledgeable by social-engineering means. The hacker will easily find a loophole to answer the question (by accessing the information you have published on social media for example) and get access to your key.
This is the point in history where 2FA comes into play to protect your identity and private information.
How Secure is Two-Factor Authentication? Let’s have a look!
Two-factor authentication can’t save your life, but what about your file?
Of course it can’t save your life, but it is another important brick added to your security wall. Here are some precautions to make the most out of 2FA protection.
1. SMS risks
Have you ever used SMS for your 2-factor authentication? Do not repeat this mistake again.
The original idea was that, if you add an additional authentication code which arrives to your smartphone, you’ll be safe since hackers have to physically steal it. The reality is quite different: it’s simple for a e-thief to move your phone number to another device, and then it is really easy to access your account. All you need is to know your mobile number and the last 4 digits of your Social Security code.
Think now if just one employee is fooled by this: all the company’s data becomes public in a matter of seconds due to human error (this is the cause of 90% of data breaches, so it’s better to prevent it!).

2. Device theft
As with anything in life, your data can be protected by multiple layers of security and 2-factor authentication. However, this doesn’t mean that your information is invulnerable.
In fact, if your device is stolen you need to take immediate action through other means in order to protect your data from theft.
3. Biometric theft
It’s 2021 and this is no longer Sci-fi stuff. We give so many permissions to access services that even our own identity marks have become a weak point.
Attackers won’t cut your finger (maybe…), but they will certainly be able to copy your fingerprint and “2-factor’s authenticate” themselves. Beware what type of 2-step verification you use.
Related reading: How to protect your privacy online: 5 actionable tips!

Some examples of two-factor authentication
Two-factor authentication doesn’t just mean having a second password, that would have implied the same weaknesses. What differentiates 2FA is the concept of “factor”: an additional way in which you prove your identity to the system. It can also be a password, but, as already mentioned a few lines above, it’s better to use a completely different way.
Below we will consider some real-life examples of how does two-factor authentication work.
Credit cards
Credit cards use 2-factor-authentication: in order to complete a transaction you need to own the card (1st factor - something you have) and know your Personal Identification Number (2nd factor - also known as the “PIN code”, something you know).
This is why PINs are so simple (consisting of only 4 numeric digits):
- the key alone + your name would be easy to hack.
- The PIN + the credit card = you have to physically steal the card AND the code.
For online payments, cards always use only one factor (i.e. data printed on the card itself). This is a risk because anyone who gets their hands on them could potentially place an order at your expense, which is why there are systems like mobile confirmation or 3D secure PIN: these are 2FA systems to protect you (and your money!) from unwanted scenarios.
Google’s USB identification
Google is not as famous for being respectful of customer data, as they make you sign in their privacy policy document. However, they do offer 2FA as a feature in all their services , plus, they are famous for having implemented a physical USB identification device in order to neutralize phishing attacks targeting their employees.
Prior to 2017, Google employees relied on a single-use key sent by Google Authenticator as a 2nd authentication factor. In contrast, this new Security Key process allowed the user to log-in easily and securely by inserting the USB and clicking a button.
As a result, none of its 85,000 employees have been victims of phishing since it adopted the keys.
N26’s location-based authentication
N26 is a Berlin-based neobank which provides customers with a free basic account and a debit card. In this scenario it’s not that uncommon for an irregular bank transaction to happen, especially with fully online services. That’s why N26 allows location tracking: this way it can immediately detect stranger transactions and block them.
However, this system can be fooled by tools like VPNs: that’s why N26 adopts location-based authentication as a complementary part of more broad adaptive authentication systems, a way that smartly considers different elements along the context of the authentication process, authenticating the user in a smooth way.
We have just seen some examples of how does two-factor authentication work. In the next section we will see how it can be implemented to make a system more secure and avoid cyber loopholes.
Setting up two-factor authentication with Cubbit
Cubbit is the first distributed cloud storage: thanks to its zero-knowledge p2p architecture it’s an ultra-secure service where no one, not even the service provider can access your stored data.
Although we offer the most secure service on the market, it’s important not to forget the simple act of logging-in with just a password and a username, the only way to access your private data. That’s why we are announcing the new “two-factor authentication” feature.
Two-factor authentication protects access to your account (and your private data), from outsiders who know your key and hacker attacks (i.e. brute force, guessing…) by adding a 2nd step to your identity verification.
But how does two-factor authentication work with Cubbit? Below are the steps to set it up - once done you can access the cloud securely, within two clicks:
N.B. Before proceeding with the steps, I ask you to choose an application that delivers you a unique authentication key every time you sign into Cubbit.
You can choose among different applications: Authy, 1Password, Last Pass Authenticator…
.gif)
1. Log-in to the Cubbit Hatch web-app by entering your username and password.
2. Click on your name in the top-right of the page.
3. Select “Profile”.
4. Click on “Privacy”.
5. Choose “Enable” in the two-factor authentication section.
6. Enter your current password and click “Next”.
7. A new window with relevant information will pop-up, read it carefully and select “Setup using an App”.
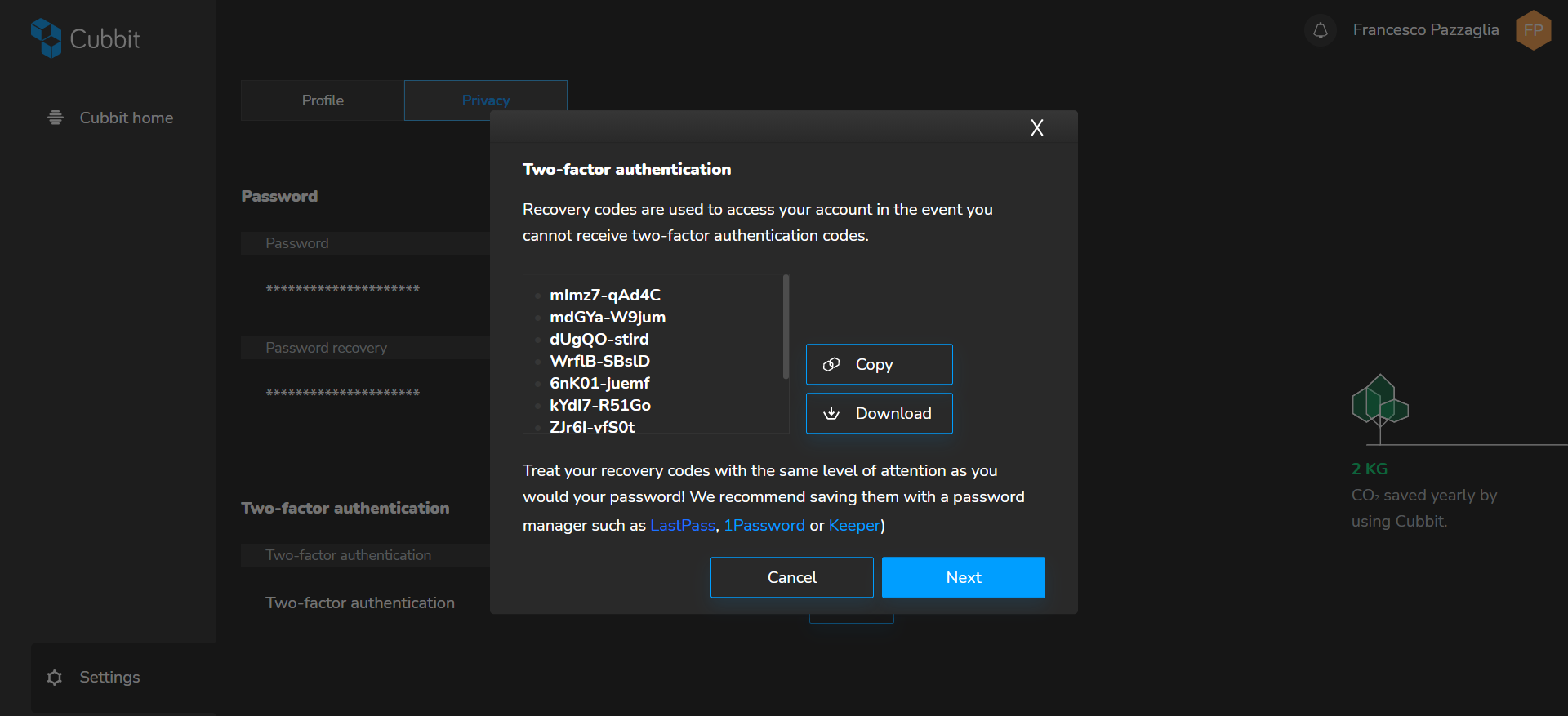
8. You will see the recovery keys on your screen. These can be used as an emergency in case you need to access Cubbit while your authentication key generator (e.g. Authy) is not available.
P.S. Save them in a safe place! Each of these recovery passwords can only be used once.
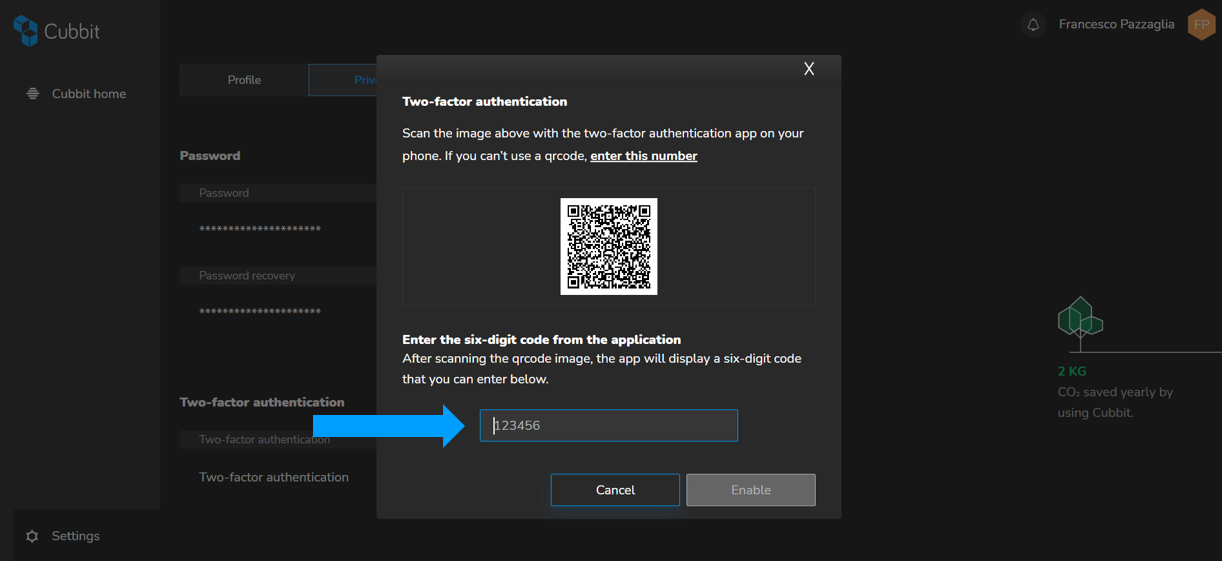
9. You will need to scan the QR code with the app of your choice (e.g. Authy, 1Password...), creating a unique six-digit sequence. If you don’t have the scanner available, you can click “enter this number” and set it manually on the authentication key generator.
10. Once scanned you will receive a code on the application, similar to the one below.
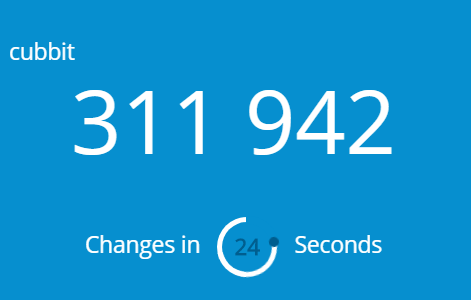
11. Type this into the six-digit code section and choose “Enable”.
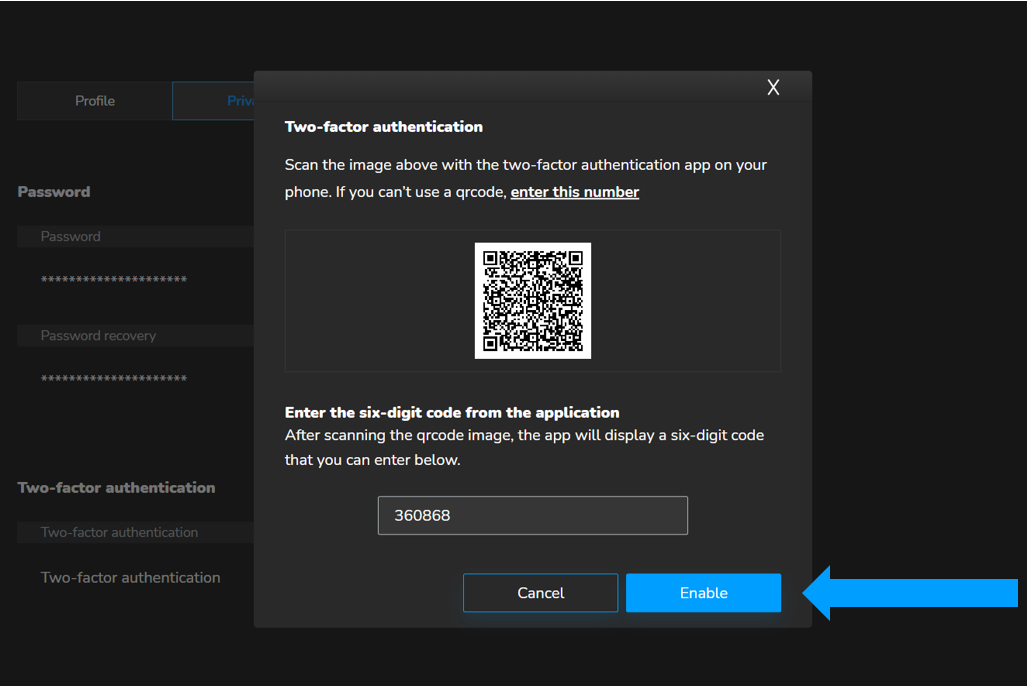
12. Your setting up of two-factor authentication is completed! Enjoy your extra layer of security ;).
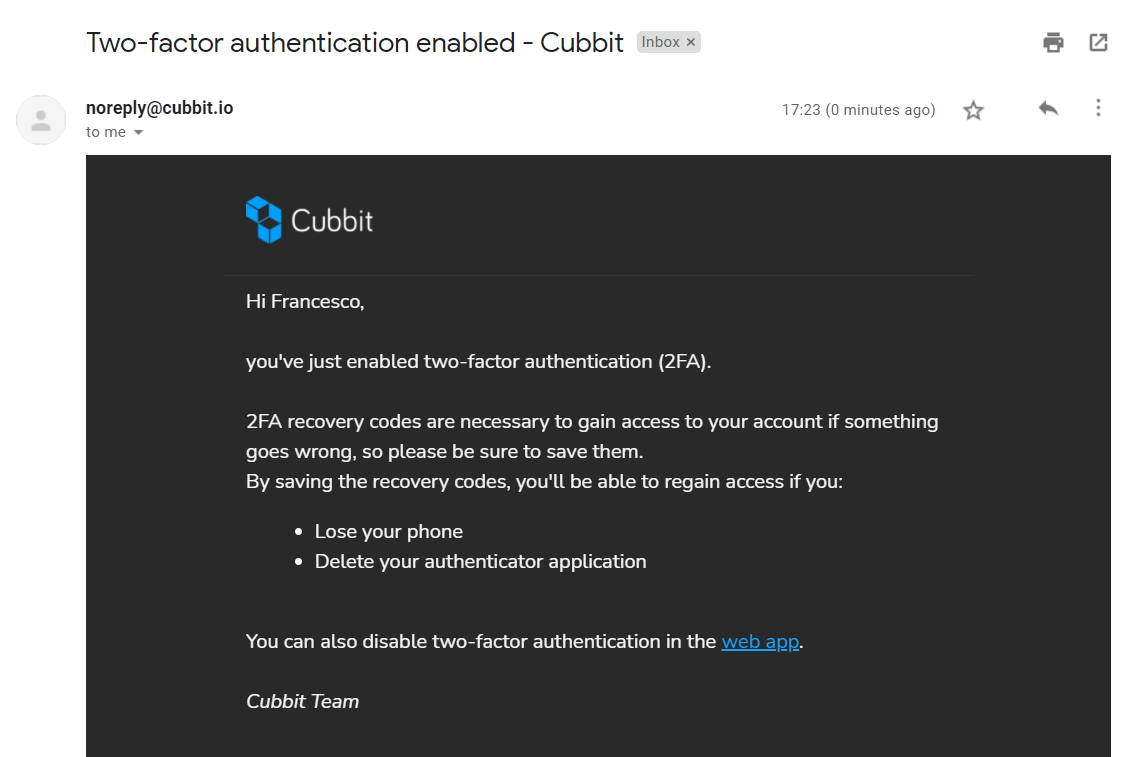
How to log-in with two-factor authentication: this is super-simple - every time you’ll log-in on your desktop or web-app, you will be asked for a 2FA code automatically generated by your app. Write it down or use one of the 10 disposable recovery keys if the authentication code generator is not available.

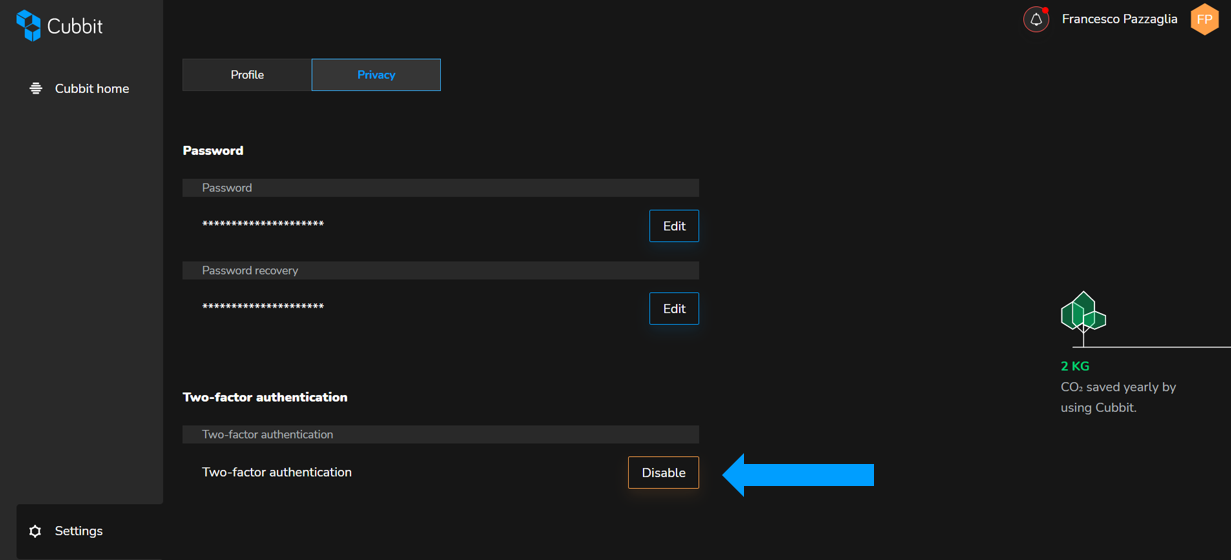
How to disable two-factor authentication: if you want to disable 2FA, simply go back to the “Privacy” section on your web-application and click on disable. You will be asked for your password and that’s it!
We hope you enjoyed the demonstration of how does two-factor authentication work and that you understood why this feature is important for protecting your data. If you have any further questions you can refer to the Help Section on Cubbit website.
To learn more about the security of your data take a look at Cubbit’s zero knowledge cloud storage page.